mcafee activate
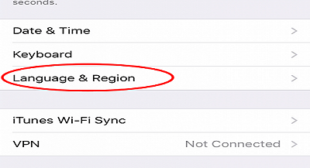
It is simple to change the language of Apple products. The language of iPhone is set in the initial setup process. If you wish to change the language on your iPhone, then read on. The method of changing the iPhone’s language settings Follow the below mentioned steps for changing your iPhone’s language settings. Firstly, go […]
Niantic has been on a streak of introducing new and exciting events for Pokemon GO fans to enjoy the title. Recently the special Lotad Day event has ended the developer team at Niantic is set to surprise Pokemon fans on this April Fools day. This April Fools day, players will be able to grab on […]
McAfee is an extremely reliable brand that offers cyber security solutions at mcafee.com/activate. After purchasing a subscription, one can download and install it on their device to get protection.
Mcafee.com/activate- Learn how to download, install and activate McAfee setup. Find the 25-digit alphanumeric product key and enter it in www.mcafee.com/activate.
Pokemon GO players have been very excited with the ongoing Raid Battles and Community Day events, but some of the Pokey trainers are not so pleased with the recently introduced Giratina Legendary Pokemon . Many gamers have been suggesting that players have been unsure of how exactly to put in use of Giratina pocket monster […]
mcafee.com/activate – Step by step procedure for installing any McAfee subscription using an activation code. Follow the easy steps given here and protect your Windows, Mac or mobile device with www.mcafee.com/activate. For any help, call McAfee toll-free number now!
In case the users wish to search the tweets on their Twitter account which includes the particular keyword, phrases or hashtags, then they can easily do so. But what should you do when you need to search an image for finding the tweets that include related pictures? Just go through the steps mentioned below to […]
Cybersecurity is the need of the day. Cyber criminals along with attackers keep conducting nefarious and malicious activities on a daily basis. From stealing credit card details to exploiting private information, the activities of malware actors are endless.